Cyber Incident Response (CIR) / Data Breach Response Services
WHAT IS DATA BREACH RESPONSE?
A data breach occurs when personal information is subjected to unauthorized access or disclosure, or where the information is lost and unauthorized access or disclosure is likely to occur.
WHAT IS PERSONAL DATA BREACH?
A personal data breach means a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, personal data. This includes breaches that are result of both accidental and deliberate causes. It also means that a breach is more than just about losing personal data.
VLS ENSURING COMPLIANCE EFFECTIVELY AND EFFICIENTLY
Incorporate a strategy suited to cyberspace to reduce reputational risk. When a cyber attack causes a breach of sensitive data, an organization's reputation and financial health must be protected by acting swiftly, comprehensively, and correctly. From data mining to breach reporting, VLS can offer a market-leading Cyber Incident Response solution that reduces compliance risk and expense.
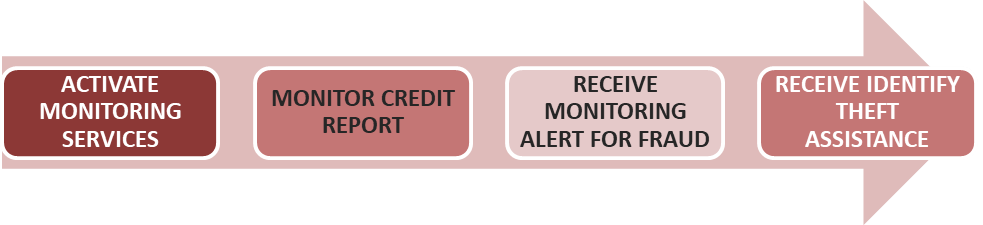
REVIEW MODEL FOR DATA BREACH
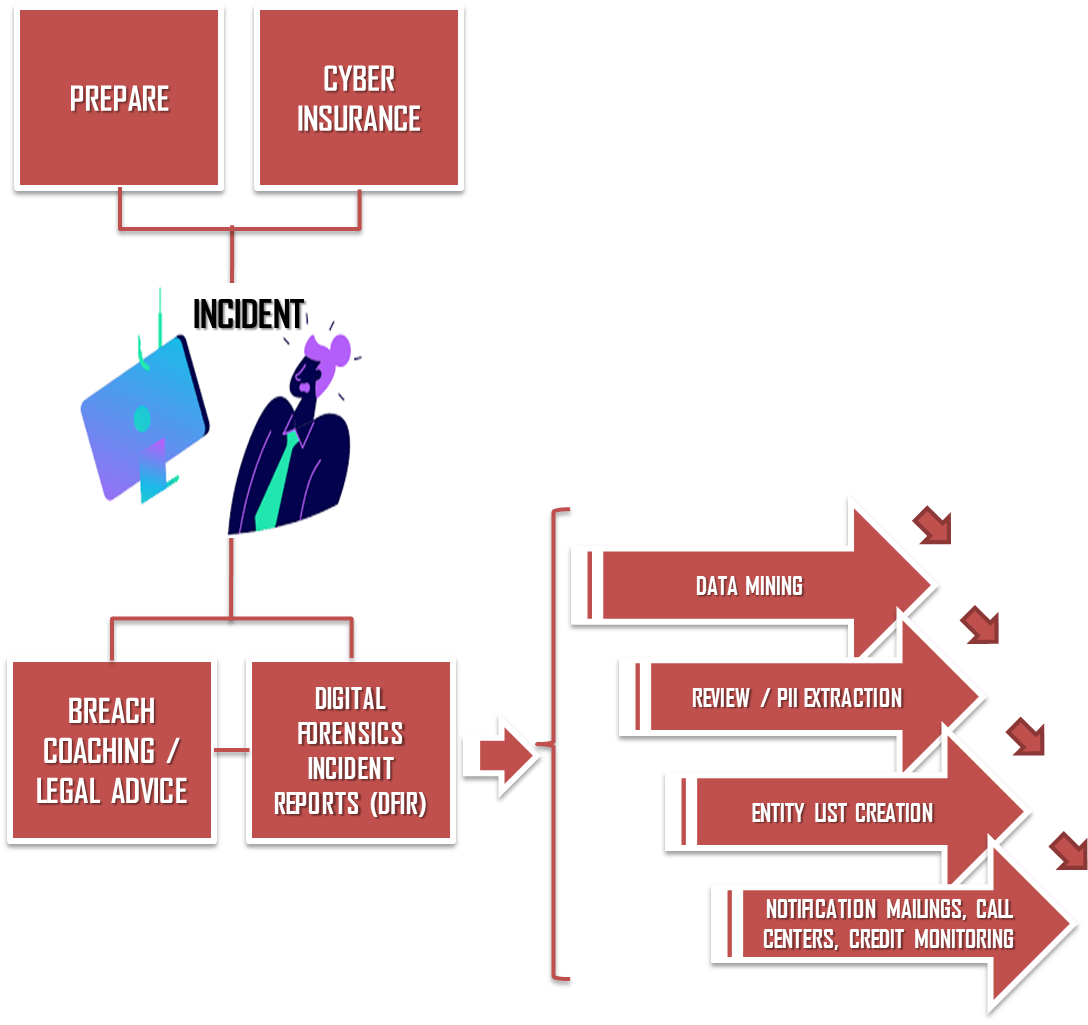
SERVICES RENDERED AT VLS
1. DATA MINING
To find pertinent data sets that need to be notified, our data mining professionals sift through vast amounts of raw breach data. By combining human experience with cutting-edge analytics and looking at datasets at a deeper level to find relevant files, we go beyond simple keyword search techniques. Multiple QC checks reduce the chance of missing important results while helping to maintain accuracy.
Here at VLS We reduce the amount of data requiring manual examination, saving you time and money.
2. REVIEW / PII EXTRACTION
At VLS we have a dedicated team and experts specializing in cybersecurity incident response within the organization that handles the data breach with the necessary expertise in compliance with applicable privacy laws and regulations.
A variety of approaches and technologies are likely to be used throughout the review and PII extraction phase. To discover and retrieve PII from the compromised data, these include data analysis tools, pattern recognition algorithms, and machine learning models.
Experts specializing in review and PII extraction with abundant tool and other algorithm knowledge needed to review.
3. Notification List Creation
VLS develops a consolidated entity list of people, businesses, and the compromised data using a tailored methodology. According to the preferences of the organisation, our resolution procedure effectively locates and combines entities, including nicknames, initials, and other linguistic and cultural variations. Then, we develop a notification list template that spells out the reportable information and the reporting procedure.
We promptly deliver notification lists while reducing waste by getting rid of duplications.
4.Mailing Notification
All customers will receive a personalized letter with their specific details on how they were impacted as part of VLS's streamlined notification procedure, making it simple to comprehend the level of exposure. Additionally, VLS verifies and updates addresses for deliverability and takes action to prevent sending the end user multiple notifications. VLS can also do an address search by name and Social Security number if an address can't be provided or further investigation is necessary to find a legitimate address.
National Change of Address (NCOA) > Address Validation > Print Quality Control > Print Staging and Mailing
5. CALL CENTRE
VLS gives you access to an English-language call centre in the US with a full team that is prepared to receive calls about your notification. Agents are trained using the offered Frequently Asked Questions, and after training has started, extra feedback is given to better clarify or address potential questions.
Frequently Asked Questions > Agent Training > Consumer Assistance